Configuring GRE Tunnels
The AirLink router can act as a Generic Routing Encapsulation (GRE) endpoint, providing a means to encapsulate a wide variety of network layer packets inside IP tunneling packets. With this feature you can reconfigure IP architectures without worrying about connectivity. GRE Tunnels in AirLink OS creates a point-to-point, unencrypted, link between routers on an IP network.
Warning: Because the GRE protocol is inherently insecure, use GRE tunnels on private networks only.
The diagram below shows the router (AirLink XR90 shown, but this example applies to any router running AirLink OS) as a GRE Tunnel endpoint. It shows two sites connected over a private network, and shows how Client A can reach Client B via GRE Tunnel.

 Initializing Table Of Contents...
Initializing Table Of Contents...Configuration
To configure GRE Tunnels:
Go to Networking > VPN > GRE Tunnels.
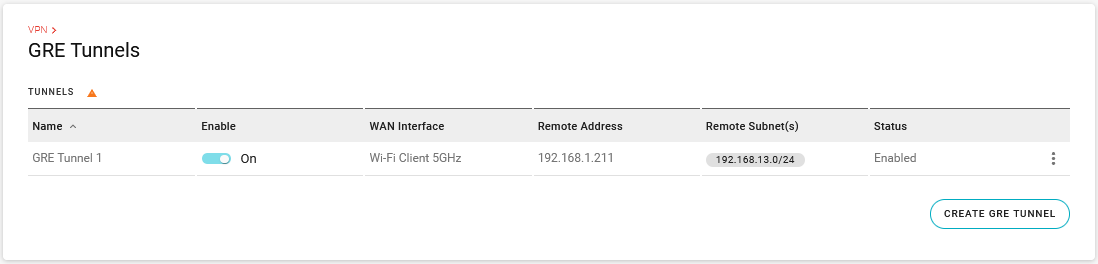
2. Click CREATE GRE TUNNEL. The Create GRE Tunnel screen appears, as shown on the right.
3. Enter the settings from the GRE Tunnel Configuration Settings table below, as required.
4. Click CREATE.
You can monitor the GRE Tunnel’s operation in the Status column in the TUNNELS table. Status is Enabled (not Connected), Connected, Disconnected (invalid configuration) or Disabled (not Enabled in the UI).
GRE Tunnel Configuration Settings
| SETTING | DESCRIPTION | RANGE |
|---|---|---|
| NAME | Name for the tunnel (GRE Tunnel 1, for example). | n/a |
| INBOUND KEY | Sets the optional GRE key for incoming encapsulated packets. Used when you have configured multiple GRE tunnels to the same Remote Address and Subnet. The remote endpoint of the tunnel must have an identical outbound key configured for this tunnel. | n/a |
| OUTBOUND KEY |
Sets the optional GRE key in the header for outgoing encapsulated packets. Used when you have configured multiple GRE tunnels. The remote endpoint of the tunnel must have an identical inbound key configured for this tunnel. |
n/a |
| ENCAPSULATION MODE | Sets the protocol for the GRE tunnel. IPv4 Tunnel or IPv6 Tunnel | IPV4, IPV6 |
| WAN INTERFACE | Sets the WAN interface used for GRE tunnel traffic (represented by WAN in the example above). The WAN interface of the router must have a “public Static IP address” (which is Internet routable, and must be able to receive packets from the Internet). | Any enabled WAN interface |
| REMOTE ADDRESS | Sets the destination IP address in the GRE header for encapsulated packets. This is the IP address for the other end of the GRE tunnel (10.156.110.150 in the example above). | IPv4 or IPv6 address, depending on the ENCAPSULATION MODE |
| REMOTE SUBNET(S) | Sets the destination subnet to route GRE tunnel traffic (“Network B” at 192.168.13.0/24 in the example above). | IP address and network prefix (CIDR format) |
| KEEPALIVE INTERVAL |
Sets a keepalive interval to determine whether the tunnel is connected. Sets the amount of time to wait between GRE keepalive packets from the VPN server gateway. If at least one packet is received within this time, the GRE tunnel status is “Connected”. |
1–3600 seconds (blank [disabled] by default) |
| KEEPALIVE RETRIES |
Sets the number of retries to determine whether the tunnel is connected. The maximum number of GRE keepalive packet tracking timeouts before the GRE tunnel status becomes “Not Connected”. |
1 to 10 (default 5) |
| LOCAL IPV4 ADDRESS | Sets the local IPv4 Address for the GRE interface. (10.0.1.1 in the example above.) | n/a |
| LOCAL IPV4 PREFIX | Enables compatibility with Cisco VPNs when multiple remote subnets are used in a single child SA. If you define multiple remote subnets under REMOTE SUBNETS, enable this setting to create a separate child SA for each remote subnet. | n/a |
| LOCAL IPV6 ADDRESS | Sets the Internet Key Exchange (IKE) mode. The default setting of IKEv2 is required for FIPS mode and MOBIKE. You may need to select IKEv1 when the router is in Client mode and a third-party VPN appliance is not compatible with IKEv2. | n/a |
| LOCAL IPV6 PREFIX | Enables compatibility with Cisco VPNs when multiple remote subnets are used in a single child SA. If you define multiple remote subnets under REMOTE SUBNETS, enable this setting to create a separate child SA for each remote subnet. | Disabled, Enabled |
| MTU AUTO-SELECT | Automatically configures MTU for the GRE Tunnel. When the tunnel is configured and enabled, this is set to 1476. | Enabled (default), Disabled |
| MTU |
You may have to decrease the tunnel MTU to adjust for the increased packet size for GRE packets. GRE adds GRE and IP headers to each packet, making them 24 bytes larger, which (if GRE MTU is left at 1500) will cause them to be fragmented or dropped when the transport MTUs in other network interfaces are set to 1500. 1,460 bytes [payload] + 20 bytes [TCP header] + 20 bytes [IP header] + 24 bytes [GRE header + IP header] = 1,524 bytes |
68–65536 (default 1500) |

