Multi-Factor Authentication
Overview
Multi-factor authentication(MFA) has been implemented on the AMM starting from version 2.17.2. The 2-factor authentication will have username and password as the first authentication, and a one time pass code (OTP) as the second authentication. There are two methods available for the second authentication.
- Email - an email is sent to the email address associated with the user account. The email will contain a one time code that the user must enter within a set period of time.
- Time-based One-time password (TOTP) - The user must enter the one time code that they receive from an Authenticator Application that has been configured for use with the AMM.
This page provides the following information:
- Requirements
- Limitations
- Configuration
- Resetting TOTP secret
- Admin users setup for MFA
- Setting the Timeout Threshold
- Setting the Retry Threshold
- User Activity Logs
Requirements
The requirements for using MFA are as follows:
If email MFA authentication is to be used:
- email access must be granted on the AMM.
- all users must have a valid email address in their profile.
If TOTP authentication is to be used:
- NTP must be configured on the AMM and the system time must be in sync with a reliable external NTP time source.
- An authenticator app must be installed and configured on a device that the user has access to.
Limitations
The limitations are as follows:
Multi-factor authentication cannot be setup on LDAP users.
Only one method of MFA can be setup per user.
Any authenticator app that is TOTP-compliant can be used. There are many authenticator apps available for mobile phones, however, users should choose an authenticator app carefully, as not all apps will properly safeguard the user’s TOTP secret. Google Authenticator and Microsoft Authenticator are the two common authenticator apps that have been tested with the AMM and were selected because of the reputation of the companies who made them. Users should exercise common online safety measures when selecting an authenticator application.
If the user deletes the authenticator app from their device or loses their TOTP secret, then they will need to contact their administrator. Refer to Resetting TOTP secret for more information.
Configuration
Configuring User to Set MFA Method to Email
To set the MFA at the user level to use Email, follow the steps below.
- Log into the AMM as an administrator user.
- Navigate to Admin > Users->select the user.
- Under Multi-Factor Authentication select Email. Then select Save.
- The user will login with their username and password. If these are successfully authenticated, the AMM will redirect the user to the verification code input page. The AMM will send a one time passcode to the user’s email address as per their user profile.
- The user will receive the one time passcode in their email and will enter the verification code on the AMM and press Submit.
- If the verification code is correct, the user will be logged into the AMM.


Configuring User to Set MFA Method to Authenticator App
To set the MFA at the user level to use Authenticator App, follow the steps below.
- Log into the AMM as an administrator user.
- Navigate to Admin > Users->select the user.
- Under Multi-Factor Authentication select Authenticator App. Then select Save.
- The user will login with their username and password. If these are successfully authenticated, the AMM will redirect the user to the TOTP registration page.
- The user will scan the QR code to add the AMM account in the authenticator app.
- The authenticator app will display a verfication code, and the user will enter it on the AMM and press Submit.
- If the verification code is correct, the user will be logged into the AMM.


Configuring Group to Use MFA
A group can be configured to use multi-factor authentication. When setting the MFA in a group, the change will cascade down to all the sub-groups and users. If any other method had been previously set, it will be overridden. When the user next logs into the AMM, they will be prompted to setup the MFA method that the administrator has set.
If some users are not to inherit the change in MFA method, then the Use group authentication settings for this user must be unchecked in the profile of the user, before the change is done in the group.

If some subgroups are not to inherit the change, then the administrator will need to set the MFA method individually on those subgroups, before the change is done in the group.
To set the MFA for a group, follow the steps below.
- Log into the AMM as an administrator user.
- Navigate to Admin >Groups->select the group.
- Under Multi-Factor Authentication, select either Email or Authenticator App. Then select Save.

Resetting TOTP secret
If the user deletes the authenticator app from their device or loses their TOTP secret, then they will need to contact their administrator.
The regular user would not normally have read/write access to Authentication under their user privileges and therefore would not be able to reset their TOTP secret. The administrator would have to reset the TOTP secret using the following steps.
- Log into the AMM as an administrator user.
- Navigate to Admin > Users > select the user.
- Under Multi-Factor Authentication select either Disabled or Email. Then select Save. This will remove the user’s previously issued TOTP secret, because it is no longer applicable.
- Edit the user again and re-select the MFA as Authenticator App. Select Save so that the AMM issues a new TOTP secret for the user.
- If the user has deleted their authenticator app, then they will need to re-install it.
- The user can login to the AMM with their username and password.
- If those are correct, then the AMM will show the MFA TOTP registration page. The user can register their authenticator app again with the newly issued TOTP secret by scanning the QR code. The user can edit their AMM login account information registered in the authenticator app.
- The user will enter the verification code displayed on the authenticator app to confirm login.

Admin users setup for MFA
If the user has read/write access to both AMM and Authentication under their user privilege settings, then the user can setup their MFA method themselves. Users with AMM and Authentication privileges are normally admin-like users.
To setup MFA method,
- Log into the AMM as an admin like user.
- Navigate to Options > Preferences page and select either Email or Authenticator App.
- If Email was selected, then any subsequent attempts to log into the AMM, will prompt them for a verification code that is sent to their email address as per their user profile.
- If Authenticator App was selected, then the user can register their authenticator app with the newly issued TOTP secret by scanning the QR code. When the user selects Save, a pop-up window will prompt the user to enter their verification code displayed on the authenticator app to confirm that it is working.
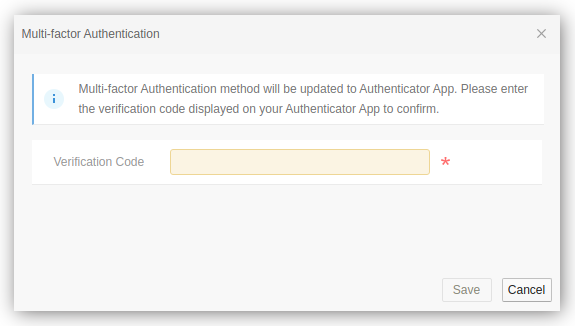
Subsequent logins to the AMM will prompt the user for the verification code from the authenticator app.
Setting the Timeout Threshold
After the AMM has authenticated the username and password, it will ask for a verification code and wait for the user to input one. The user must submit a verification code within the configured timeout threshold (default 2 minutes). If the page times out, the user will be redirected back to the login page with an error code: Correct verification code was not entered before timeout.
The timeout threshold can be configured in the web.xml file with the following entry:
<context-param>
<param-name>inmotion.mfa.timeout.inseconds<param-name>
<param-value>120<param-value>
<context-param>
Setting the Retry Threshold
If the user enters the wrong verification code, the AMM will allow the user to retry for a configured maximum number of retries (default is 3). If the user enters the incorrect code more than the configured number of retries, then the user will be redirected back to the login page with an error code: Too many failed attempts with incorrect verification code.
The retry threshold can be configured in the web.xml file with the following entry:
<context-param>
<param-name>inmotion.mfa.maximum.retrys<param-name>
<param-value>3<param-value>
<context-param>
User Activity Logs
In addition to existing user activity entries on login, the following MFA user activity logs are created and visible in Admin > User Activity.
| Event | Message |
| User pre-authenticated with password, awaiting verification code | Login pre-authenticated, await verification. MFA method: Email|Authenticator App |
| MFA login successful | Login verified. MFA method: Email|Authenticator App |
| MFA login encountered an error | Login error. MFA method: Email|Authenticator App, MFA error: Error message |
The following table lists common errors messages.
| Error Message | Description |
| Correct verification code was not entered before timeout. | User did not enter the correct verification code before the timeout threshold expired. |
| Incorrect verification code. | User did not enter the correct verification code. |
| Too many failed attempts with incorrect verification code. | User entered the incorrect verification code too many times. |
 Searching...
Searching...
