Configuring Network Address Translations
Network Address Translation (NAT) rules are used to map private IP addresses within a local network to a single IP address for communicating with external networks. You can define NAT rules through Networking > Firewall > Network Address Translations.
The Network Address Translation table shows the user-defined rules.

| SETTING | DESCRIPTION |
|---|---|
| ENABLED | Set to ENABLED if rule is to be used as soon as it is saved. |
| RANK | Order in which the rules are applied to outgoing traffic. Lowest rank is applied first. Rank must be greater than zero. |
| NAME | Name assigned to the rule |
| OUTPUT INTERFACES | Outgoing traffic Zones (System Zones or your own defined zones) or interfaces on which the rule will be applied |
| SOURCE IP(S) | Private IP address assigned to a device within the local network. Optional. |
| DESTINATION IP(S) | IP address of the target device or server on the external network. Optional. |
| ACTION |
|
| STATUS |
Note: By default, the AirLink router uses NAT and masquerades traffic out of the WAN interface using the outgoing WAN IP address. You can disable the default behavior through Networking > General > WAN > <Edit Device> > Masquerade. In the absence of defined NAT rules, this setting will dictate the course of action for handling the traffic. Outgoing traffic is first matched against the User NAT rules. If none of the rules are applicable for the traffic, the WAN masquerade setting (if any) will then be applied to this traffic.
To configure a Network Address Translation rule:
Go to Networking > Firewall > Network Address Translations.
Click CREATE SNAT RULE to create a new rule, or click Edit at the end of a row to update an existing rule.
Begin configuring the Source Network Address Translation rule.
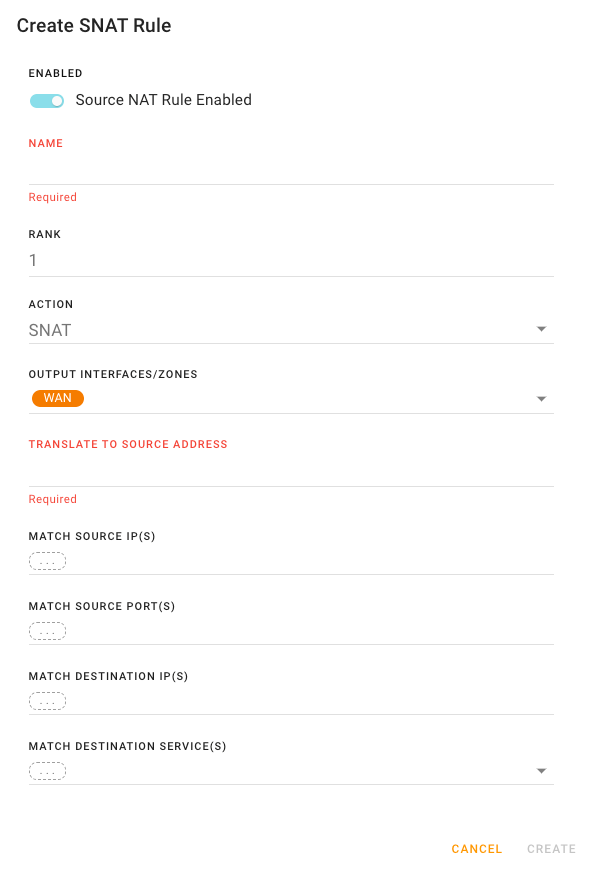
If you want the rule to be used as soon as it is saved, ensure ENABLED is selected to activate the rule.
Enter a unique NAME to identify the rule when it appears in the NETWORK ADDRESS TRANSLATIONS table.
Enter the rule’s RANK.
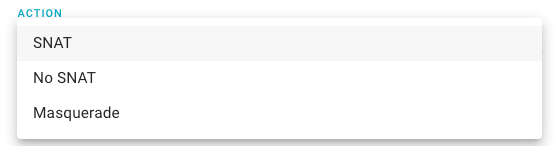
Select the ACTION.
Click the OUTPUT INTERFACES/ZONES field to select the specific outgoing traffic Zones (System Zones or your own defined zones) or interfaces on which the rule will be applied. Add as many zones and interfaces as you want. (Note that NAT is typically performed on outgoing WAN traffic.)
Tip If only specific interfaces require forwarding, use narrowly focused zones instead of all-encompassing zones. For example, if the WAN zone is selected, port forwarding is performed for all WAN devices. However, if only two specific WAN interfaces need to be forwarded, create and use a zone containing only those specific interfaces.

For TRANSLATE TO SOURCE ADDRESS, enter the source IP address.
In addition to the settings described above, you can configure the following settings:
Optionally enter the MATCH SOURCE IP(S). Only traffic based on the source IP address(es) will follow this SNAT rule.
Optionally enter the MATCH SOURCE PORT(S). Only traffic using the source port number specified will follow this SNAT rule.
Optionally enter the MATCH DESTINATION IP(S). Only traffic that is being directed to the destination IP(s) will follow this SNAT rule.
Optionally select the MATCH DESTINATION SERVICE(S). The SNAT rule will apply only to traffic that is identified with the specified service. More than one service can be selected as shown below.

Note: The MATCH SOURCE IP/DESTINATION IP/SOURCE PORTS/DESTINATION SERVICES are all AND operations. For example, Match source IP and Destination IP and Source port.
Tip To limit access to specific computer devices or networks, create and use a source IP/Network with an appropriate source IP address range. For example, to allow access only to the computer devices on a private APN network, a source address range like 10.10.0.0/24 could be used.
 Searching...
Searching...



